2024
| Program | Speakers | Sponsors | Registration | Team |
General Information
The Elbsides 2024 computer security community conference will be held in Hamburg, Germany on Friday, the 13th of September. Meanwhile, we need sponsors to make this event possible and keep the costs for the participants low. If you are interested in sponsoring, please contact us at elbsides -at- gmail.com.
The Call for Papers is now open, and we welcome your presentation submission until the end of July 7th. is now closed. Thank you for all your proposals, and we hope to see you in Hamburg!
Location
This year Elbsides will be at the river Elbe: at the Empire Riverside Hotel, a 4-star hotel in the heart of Hamburg. The hotel is located in the St. Pauli district, near the Reeperbahn and overlooking the port of Hamburg. The conference will be held in the hotel’s conference center.
Pictures © Empire Riverside Hotel, Stefan Karstens and Andrea Flak
Follow us
- Mastodon: @elbsides@infosec.exchange
- Bluesky: @elbsides.bsky.social
- LinkedIn: linkedin.com/company/elbsides
If you haven’t been to Elbsides 2023 - see what you missed and watch the talks on our 2023 Youtube channel
Sponsors
We hope to welcome many old and new sponsors to make this event possible with minimal costs for attendees and to keep this event as inclusive as possible. If you are interested in sponsoring, please contact us at elbsides -at- gmail.com.
 |
 |
|
Program
Backup talks:
- Santi Abastante: Dredge: A Open Source Framework for Cloud Incident Response
- Thore Tiemann: “Act natural!”: Exchanging Private Messages on Public Blockchains
Speakers
Álvaro Martínez, Candid Wüest, Christian Kollee, Hilko Bengen, Katharine Jarmul, Marc Ratfeld, Marit Hansen, Max Maaß, Michael Helwig, Paul Vixie, Sam Macdonald, Santi Abastante, Stefan Hager, Thore Tiemann, Tim Walter, Timo Pagel
Álvaro Martínez

Álvaro Martínez holds a Bachelor of Engineering in Telecommunications and a Master’s degree in Information Security, graduated in 2018. After several years working as web developer, he decided to switch to his preferred area, cybersecurity, where he currently works at conducting vulnerability assessments and web penetration tests, integrating security tools into corporate environments and helping development teams to better understand and mitigate vulnerabilities in their applications.
Candid Wüest

Candid Wüest is a seasoned cybersecurity expert with a strong blend of technical skills, leadership, and over 25 years of passion in the field of security. He currently serves as an independent security advisor for various companies and the Swiss government. Previously, he was the VP of Cyber Protection Research at Acronis, where he led the creation of the security department and the EDR product. Prior to that, he spent over sixteen years at Symantec, where he played a key role in building their global security response team as the technical lead, focusing on malware and threat analysis. Wüest has authored a book and several white papers and has been recognized as a security expert in top-tier media outlets. He frequently speaks at major security conferences, including RSAC and BlackHat and is an organizer of AREA41 & BSides Zurich. He began learning coding and English on a Commodore 64. He holds a Master’s degree in Computer Science from ETH Zurich and possesses various certifications and patents.
Christian Kollee
Christian currently works as a Network Detection Engineer in the German finance sector. Previously, he worked as a forensic analyst and incident handler in international organizations and medium-sized German businesses. With more than ten years of experience in IT security, Christian knows the problems of all IT security types, from medium-sized companies to DAX30 corporations. Shortly, he will join a company doing Incident Response and Managed Detection & Response. Besides learning about new attacker tools and techniques, he tries desperately to reduce his ever-growing stack of articles and books in his spare time.
Hilko Bengen
Hilko works in the CSIRT for a transportation and logistics company. He feels most comfortable when thinking about problems that touch systems programming, operations and IT security. For more than 25 years, he has learned to take free and open source software for granted, and he is still amazed when he hears how others have found his contributions useful.
Katharine Jarmul

Katharine Jarmul is a privacy activist and an internationally recognized data scientist and lecturer who focuses her work and research on privacy and security in data science and machine learning. You can follow her work via her newsletter, Probably Private or in her recently published book, “Practical Data Privacy” (O’Reilly 2023) now also available in German as “Data Privacy in der Praxis.”
Marc Ratfeld

- LinkedIn: Marc Ratfeld
- Talk: Protecting the energy transition
Marc Ratfeld is a computer scientist, CISSP, GIAC and ISMS Senior Consultant. With over 25 years of experience in the field of information security, Mr. Ratfeld has worked in various industries as an information security officer and helps companies to implement and continuously develop information management systems. In doing so, he pays particular attention to the practicability of implementation and has successfully brought ISMS implementation projects to the level of certification. Since 2023, he has also been an executive manager of pure ISM GmbH.
Marit Hansen

- Closing keynote: How to implement data protection – fulfilling the (not so new) requirement of the GDPR
Dr. h.c. Marit Hansen has been the State Data Protection Commissioner of Land Schleswig-Holstein and Chief of Unabhängiges Landeszentrum für Datenschutz (ULD) since 2015. Before being appointed Data Protection Commissioner, she had been Deputy Commissioner for seven years. After graduating with a diploma degree in computer science in 1995, Marit has been working on privacy and security aspects. Her focus is on “data protection by design” and “data protection by default” from both the technical and the legal perspectives.
Max Maaß

- Mastodon: @hacksilon@infosec.exchange
- Talk: Protectors of the Realm: Breaking and Fixing Keycloak Configurations
Max Maaß works at the security team at iteratec. He spends his time with architecture reviews, threat modeling and pentesting for software development projects, and has contributed to the OWASP secureCodeBox. Previously, he conducted research into security and privacy issues at the Secure Mobile Networking Lab at TU Darmstadt.
Michael Helwig

With a background in software development, Michael is a cybersecurity strategist and expert on a wide range of product and cybersecurity topics. He is the co-founder of a security consulting firm that helps clients across industries implement product security programs, adopt DevSecOps, and achieve compliance with information security standards and privacy requirements. He is currently exploring the impact and potential of AI on secure development-related security practices. He believes that people and communication are at least as important and effective in moving organizations forward as tools and technology, and that security is best achieved when linked to software development and business interests.
Paul Vixie

- Talk: The evolution of cloud security
- Twitter: @paulvixie
Paul Vixie is a VP and Distinguished Engineer who joined AWS Security after a 29-year career as the founder and CEO of five startup companies covering the fields of DNS, anti-spam, Internet exchange, Internet carriage and hosting, and Internet security. Vixie earned his Ph.D. in Computer Science from Keio University in 2011 and was inducted into the Internet Hall of Fame in 2014. He is also known as an author of open-source software including Cron. As a VP, Distinguished Engineer and Deputy CISO at AWS, Paul and his team in the Office of the CISO use leadership and technical expertise to provide guidance and collaboration on the development and implementation of advanced security strategies, risk management, and helping customers be secure in the cloud.
Sam Macdonald

A cybersecurity professional from the UK whereby imposter syndrome is a weekly bi-product of having changed careers midlife. Every day is a school day, now looking to tackle the inner fraud that takes so many in the community and share what I have learnt.
Santi Abastante

Ex-Police Officer from Argentina, Cloud Incident Responder and Security Engineer with 10+ years of IT experience.
Stefan Hager

Stefan works for the Internet Security Team at German company DATEV eG. He started messing with computers in the 80s and turned it into a job as a programmer in the early 90s. Since 2000 he has been securing networks and computers for various enterprises in Germany and Scotland. His main focus nowadays is security research, raising security awareness, coming up with creative solutions to security problems and discussing new ideas concerning threat mitigation. When not trying to do any of the stuff mentioned above, he is either travelling, producing hacker music and other electronic beats or gardening.
Thore Tiemann

- Mastodon: @thoretiemann@infosec.exchange
- Talk: “Act natural!”: Exchanging Private Messages on Public Blockchains
Thore Tiemann is a research assistant and PhD student at the Institute for IT Security at the Universität zu Lübeck. His research interests are in the area of computer and systems security with a focus on microarchitectural side-channel attacks and defenses in heterogeneous cloud computing.
Tim Walter

- Mastodon: @twwd@infosec.exchange
- Talk: Protectors of the Realm: Breaking and Fixing Keycloak Configurations
After working as a full-stack developer and software architect, Tim Walter now works as a security architect for iteratec. His primary task is to support teams in the development of secure software through threat modeling, security reviews of architecture concepts, vulnerability analyses and the integration and automation of security scans.
Timo Pagel

Timo Pagel has been in the IT industry for over twenty five years. After a career as a system administrator and web developer, he advises customers as a DevSecOps consultant and trainer. His focus is on integrating security into the development lifecycle. For example with security test automation for software and infrastructure and assessment of complex applications in the cloud. In his spare time, he teaches “Web and Application Security” at various universities of applied sciences.
Talks
AI (In)security: How to (Still) Successfully Attack an AI System
Opening Keynote
Speaker: Katharine Jarmul
In this talk, we’ll review attacks on today’s “AI” systems, and how fundamental aspects of adversarial examples are still relevant today. We’ll explore how purple-teaming AI systems could work, and the latest research on potential preventative measures and a few common-sense tips, if your CEO tells you, you have to deploy an AI-based application.
Video
Unveiling the Reality: The True Impact of GenAI on Cybercrime
Speaker: Candid Wüest
Are we on the brink of a GenAI-powered cybercrime apocalypse? Sensational headlines may stoke fear, but the reality is more nuanced. Join us to explore the true impact of GenAI on cybercrime, debunk myths, and reveal insights from the frontlines. We’ll start with the infamous $25 million BEC deepfake video conference scam, illustrating how deep fakes are weaponized. From son-in-trouble scams to 2-for-1 bitcoin videos, we’ll uncover the various deepfake threat landscape. Next, discover how GenAI transforms phishing attacks, personalizing messages and orchestrating interactive schemes like romance scams. See how cybercriminals leverage GenAI for automation and efficiency, ramping up malicious operations. We’ll demystify AI-generated, AI-supported, and AI-powered threats, showing how AI accelerates threat distribution through script creation and scaling. Real-world examples of GenAI-generated malware will be discussed. Like for example the polymorphic or rather metamorphic PoC malware Black Mamba, that dynamically adapts using LLMs. Even nation state APTs have played with it. We’ll explain why these threats remain detectable with current methods and why the feared Terminator ransomware isn’t on the horizon for this year. Discover the strategic shift from creating unfiltered LLMs, like FraudGPT, to offering proxied prompt injection into existing models, like LoopGPT. See how tools like FuzzAI help with new prompt injections. Finally, we’ll touch on the MITRE ATLAS framework and discuss related techniques, e.g. adversarial AI attacks, setting the stage for future discussions. This talk separates hype from reality, providing a clear perspective on the evolving cyber threat landscape driven by GenAI.
Slides
Video
Far beyond the perimeter - exploring external attack surfaces
Speaker: Stefan Hager
Looking for intel in all the right places is an art that adversaries seem to have mastered; but when it comes to their own data, many companies seem to lose interest in examining anything that’s outside the “perimeter” - whatever that is supposed to be nowadays. Credential leaks, shadow IT, unofficial websites with official info - the list of assets far outside the data centers of companies is long, and those assets nevertheless pose risks. Instead of turning a blind eye, it’s important (and necessary) to get an understanding of what kind of information is out there, ready to be used or abused and protect accordingly. What risks are “out there” and what is meant by “out there”? How can those risks be addressed? What tools are easily available?
Slides
Video
Key Steps to Achieving an Application Security Program
Speaker: Timo Pagel
This talk outlines a practical approach to building and optimizing application security (AppSec) programs for organizations of all sizes. While briefly touching on foundational elements, the presentation focuses on developing and implementing a custom organizational maturity model that resonates with development and operations teams. Moving beyond traditional frameworks, attendees will learn to design tailored models that account for diverse operating environments. The talk provides strategies for avoiding common pitfalls, implementing effective metrics, and creating a scalable AppSec approach adaptable to an organization’s evolving needs. Through actionable advice and real-world examples, participants will gain insights applicable to both new and existing AppSec programs.
Video
Dealing With Imposter Syndrome
Speaker: Sam Macdonald
Imposter syndrome is a psychological phenomenon where individuals doubt their accomplishments and fear being exposed as a “fraud,” despite evidence of their competence and success. It can affect anyone, regardless of their career stage, background, or achievements.
Slides
Video
Ready to Respond - Plan, Prepare, Try & Train
Speaker: Christian Kollee
“Prevention eventually fails.” and “Assume breach.” are two statements the IT security community agreed on long ago. These statements are still valid, especially with the recent vulnerabilities in security devices from different vendors. According to Mandiant M-Trends 2024 Special Report, exploiting vulnerabilities is globally the initial access vector in 38% of all intrusions, followed by Phishing (17%) and access provided by a prior compromise (15%). Over the last two to three years, many of these vulnerabilities have also concerned security devices like firewalls, VPN gateways, and other Internet-connected devices.
Therefore, being ready to respond to a cyberattack must be a priority for enterprises of every size. But what does “being ready” really mean? There are three distinct phases an enterprise needs to go through to be ready. The first phase is the usual You need a plan, which usually means creating documents that describe how to conduct an incident response, who is responsible, and who needs to be informed. However, more than just having a plan is required. Preparing your people, processes, and environment is the second step for a successful incident response. Do your people have the required skills? Are your processes aligned with suppliers and service providers? Do you have the tools in place to perform the incident response? Finally, you need to practice and train every emergency. There are different possibilities for conducting incident response engagements, from simple tabletop exercises to full-blown emergency exercises. Each of them has its advantages and drawbacks.
In this talk, I’ll review these three phases and present the essential points based on my experiences. From creating a plan to the preparation phase to implementation and training, we will look at the crucial steps in a brief overview.
Slides
Video
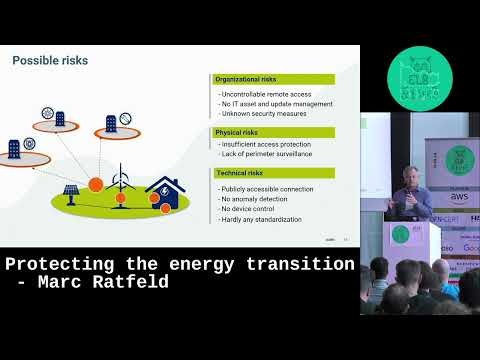
Protecting the energy transition
Speaker: Marc Ratfeld
The renewable energy sector is one key factor within critical infrastructure of Europe and Germany. Protecting this industry against cyberattacks is a constant challenge. The rapid growth and increased security requirements are putting the industry under constant pressure to adapt. This talk will give you an insight view of actual attempts to protect IT and OT environments off- and onshore.
Slides
Video
Help, my application is vulnerable, but how bad is it?
Speakers: Michael Helwig, Álvaro Martínez
With an increasing number of high and critical security vulnerabilities being disclosed each year, it is a constant challenge for developers and project teams to respond quickly to serious vulnerabilities in their code base and projects. Often there is no structured process in place to deal with the issues and a decision needs to be made quickly. What can you do?
In this presentation we will explore different approaches to quickly analyze vulnerabilities and estimate the potential impact in your specific context. CVSS scoring is often used as a first step in prioritization, but what is CVSS? Thanks to artificial intelligence, we now have EPSS scoring to help us prioritize, but does it really improve our situation? Ultimately, you have to take your architecture and technical context into account to come to the right conclusion? For this we will take a look at Cyber Kill Chains and how they can be used for this purpose.
The goal of this presentation is to give developers practical insight into the vulnerability analysis process and to provide them with ideas and tools they can use when the next vulnerability appears.
Video
Detection And Response for Linux without EDR
Speaker: Hilko Bengen
In modern, networked, enterprise IT environments, the focus of defense teams has shifted from monitoring network infrastructure towards endpoints. Installing endpoint detection and response (EDR) software on user workstations and servers – and actually monitoring their activities and findings – has become an easy default choice.
However, it appears that in development of most EDR products, with their heritage in antivirus software, a very Windows-centric worldview is retained. Support for other operating systems, especially Linux, seems to come as an afterthought, leaving visibility gaps that may be easily exploited by skilled attackers.
After evaluating several EDR vendors’ products specifically for use in a large, heterogeneous Linux server landscape, we found that the capabilities were no match to our existing near-real-time detection mechanisms. We couldn’t even replicate our previous work using the products. Deciding against any EDR product meant that we need to find an alternative approach to building out response capabilities.
This talk illustrates mostly home-grown approaches to detection and response engineering that provide analysts with tools for generating context and for large-scale threat hunting while making it as pleasant as possible for operations teams to integrate the required components into their systems.
Video
Protectors of the Realm: Breaking and Fixing Keycloak Configurations
Speakers: Max Maaß, Tim Walter
Keycloak is a widely used tool for authentication and user management in many projects and is therefore often encountered in security audits. However, analyzing the security of an existing Keycloak instance is often a challenge due to the complexity of the software and its configuration options.
Having been responsible for the security of a Keycloak instance in a large software project for almost two years, we share our insights on what to look for. We also present our open source Keycloak configuration auditor kcwarden, which we developed to facilitate our work. The tool can detect common security issues and can be easily customized to detect project-specific issues, such as dangerous role assignments or policy violations. This allows us to continuously monitor the configuration for dangerous changes that might otherwise go unnoticed.
After attending this talk, you should have an overview of common Keycloak misconfigurations and how you can use kcwarden to support your work.
Video
Dredge: A Open Source Framework for Cloud Incident Response
Speaker: Santi Abastante
BACKUP TALK
Cloud incident response can be daunting, requiring a plethora of tools and skills, while most Cloud Based Startups can’t allocate budget for preventive controls, there is less space for them to understand what to do if they are hacked.
That’s why I created Dredge, an Open Source framework designed to streamline cloud incident investigations, by allowing Cloud Engineers and Incident Responders to execute non-trivial response tasks effortlessly, irrespective of your familiarity with specific cloud platforms nor incident response tactics.
The main idea is to empower engineers to respond to attacks no matter what preparation they had before, taking advantage of most of the out-of-the box security features cloud providers offer but not everybody is aware, like being able to retrieve a forensic image from a running server or getting logs that they didn’t know they had.
Some Key Features that differentiate Dredge from existing tooling:
- Python-based CLI
- Retrieve logs seamlessly from Github, Kubernetes, AWS, GCP or Azure.
- Take action: whether it’s blocking an IP in an AWS tenant, disabling an AccessKey, isolating an EC2 instance, or strategically extracting crucial post-compromise user data.
- Identify tactical misconfigurations that can be exploited by an attacker.
- Create an attack timeline based on IOCs.
- Analyze retrieved data effortlessly within your terminal, utilizing built-in capabilities from VirusTotal and Shodan.
- Cloud Incident Response Guidelines for companies to embrace and build their playbooks.
“Act natural!”: Exchanging Private Messages on Public Blockchains
Speaker: Thore Tiemann
BACKUP TALK
Messengers have become an essential means of interpersonal interaction. Yet untraceable private communication remains an elusive goal, as most messengers hide content, but not communication patterns. The knowledge of communication patterns can by itself reveal too much, as happened, e.g., in the context of the Arab Spring. Subliminal channels in cryptographic systems enable untraceable private communication in plain sight. In this context, bulletin boards in the form of blockchains are a natural object for subliminal communication: accessing them is innocuous, as they rely on distributed access for verification and extension. At the same time, blockchain users generate hundreds of thousands of transactions per day that are individually signed and placed on the blockchain. Thus, blockchains may serve as innocuous repository for publicly accessible cryptographic transactions where subliminal channels can be placed. This significantly increases the availability of publicly accessible cryptographic transactions where subliminal channels can be placed.
In this paper, we propose a public-key subliminal channel using secret-recoverable splittable signature schemes on blockchains and prove that our construction is undetectable in the random oracle model under common cryptographic assumptions. Our approach is applicable to any secret-recoverable splittable signature scheme and introduces a constant overhead of a single signature per message. Such schemes are used by 98 of the top 100 cryptocurrencies. We also analyze the applicability of our approach to the Bitcoin, Monero, and RippleNet networks and present proof of concept implementations for Bitcoin and RippleNet.
The evolution of cloud security
Special Guest talk
Speaker: Paul Vixie
There was a time when it was reasonable to ask how an organization’s data and processing could possibly be as secure running on someone else’s computer (in the cloud) as it would be in privately owned and operated servers, days centers, and networks. These days that question has been inverted, and we must ask how hosting a workload within privately operated infrastructure could possibly be as secure as putting that workload into the cloud. Let’s discuss.
Video
How to implement data protection – fulfilling the (not so new) requirement of the GDPR
Closing Keynote
Speaker: Marit Hansen
The concept of “privacy by design” has been discussed for several decades. The same holds for “security by design”. The general idea is to implement the requirements derived from privacy or security from the very beginning of the engineering process for software, and also hardware where appropriate. Meanwhile, Article 25 of the General Data Protection Regulation demands both “data Protection by design” and “data protection by default” from data controllers, i.e. the entities responsible for the processing of personal data. In the talk, Marit will clarify the legal obligation stemming from the GDPR and show how to fulfill this requirement in practice.
Video
Team
Morton
Morton is a researcher in the Forward-Looking Threat Research (FTR) team at Trend Micro, Inc. where he peers into the future of computers and society to identify the risks and vulnerabilities of the future. His past in computer security stretches back 30 years and he has been involved in most of the innovations in security, first at the University of Hamburg, Germany, then IBM Research and now Trend Micro. While originally active in malware analysis and computer forensics, recently his team has been focussing on massive threat data analysis for spotting new types of attacks quantitatively and also on modelling future threats to society that will accompany its inevitable march towards tighter integration in smart cities, intelligent transportation, supply chains and manufacturing. Morton, a native of New York City, has a Computer Science PhD degree from the University of Hamburg, and resides in the Hamburg, Germany area.
Dagmar
Coming from a non-technical background, Dagmar brings her knowledge of event organization to Elbsides. Through previous experiences in professional stage management / production for theatre in the UK and US, as well as Sci-Fi conventions in Germany, she teamed up with her husband Morton to organize events for the computer security industry, BSides Munich being among them. Having lived and worked in a variety of countries, she enjoys traveling the globe and seeing theatre productions, especially in London.
Stefan
For all his professional business life (even years before that) Stefan has been involved in information security. In 1993 he was the first student to be hired by the freshly launched DFN-CERT Services GmbH, the first Computer Emergency Response Team in Germany and also one of the first within Europe. After having spent a number of years in the PKI universe he worked as an IT security consultant for the next 15 years before re-joining the awesome crew at DFN-CERT Services GmbH in 2016. He likes IT forensics, Cyber Threat Intelligence, and malware analysis and loves helping people.
Florian
A past interest in archaeology brought Florian to the field of security. To him, both share a similar approach: recognizing the ideas of the past via its artifacts and the application of these lessons to form a better future. As a security engineer he tries to adopt this philosophy to the various aspects of the field, may it be user awareness, OS and network security or how to cloud securely. He also enjoys spicy food, fast bikes and open source.
Debbie
Debbie is also a non-techie. Her passion for working in IT security started in 2019 with SCHUTZWERK, where she came into contact with Elbsides. She has been involved in the community ever since. Inspired by her former colleagues at SCHUTZWERK, she also started studying business informatics part-time in March 2021 to gain more IT knowledge. During her studies, which will end in fall 2024, she has left no opportunity to combine all topics with IT security. From June 2024, Debbie will be working as an Account Manager at AirITSystems. Her colleagues and her ensure that companies’ business-critical IT functions securely and smoothly. She is very much looking forward to this as she will be delving even deeper into the IT world.
Jonas
Jonas’ day job is in incident response and forensics at BlackBerry. During engagements he specializes in disk forensics and fast triage, relying heavily on automation to aid in fast recovery of customers affected by data breaches or malware incidents. In his spare screen time he engages in various open source efforts and likes researching new forensics related topics. Reverse engineering proprietary APIs, file formats and protocols is one of his main interests. In the great outdoors he enjoys geocaching and paddling. He also added aerial photography and semi-autonomous to fully manual flight with home-built UAVs and FPV drones to his outdoor activities.
David
David is an independent software developer, penetration tester and IT consultant. He likes to build software, analyze systems and troubleshoot weird computer problems. When not in front of a screen he enjoys a good physical challenge, doing various kinds of sports.
Fabian
Fabian currently works as an embedded software engineer for a small company in Northern Germany. He was working as a financial consultant when his fascination for technology led him back to school to study electrical engineering and digital systems. During his bachelors and master’s thesis he was able to get deep into the weeds of reverse engineering and secure code as part of the vulnerability analysis department at NXP. Whenever he isn’t sitting in front of a keyboard, he enjoys playing music and sports outdoors.
Matthias
Matthias has more than 25 years of experience in various industries, disciplines and roles in the world of IT. He now uses this experience as a freelance cybersecurity culture evangelist to support organisations on their way to becoming secure and resilient organisms. This has a lot to do with the agile mindset, where people take centre stage - processes ensure smooth interaction and technology is seen as a tool, not an end in itself! Apart from that, he likes to spend his time outdoors, preferably exploring new holiday destinations or cycling in the surrounding area.
Peddy
Peddy has been working with Unix systems since the early 1990s and set up and operated one of the first web servers in Germany. He was the first to introduce Hamburg teachers to the Internet and installed the first Linux servers in Hamburg schools. He did the same in a software company for private health insurance. Security during implementation, as well as training, was always an issue. At his current employer, a media company, security in the cloud environment is a top priority.
Georg
- LinkedIn linkedin.com/in/georgpheheise
- X: @gpheheise
Georg is the Lead Penetration Tester and Technical Head of the Advanced Cyber Security Team at Lufthansa Industry Solutions. With a strong passion for Red-Teaming and Active Directory testing, he has led his team to deliver many security assessments, including vulnerability scans, web application tests, corporate network audits, and advanced Red Team engagements.
Georg’s extensive experience spans German and Australian markets, where he has worked with major multinational corporations and Fortune 500 companies.